Div Friday, a virus known as WannaCry infected machines across countries. It’s known as how much money did wannacry make which is a malicious piece of software that encrypts a user’s files then demands them pay money to unlock. ET on Monday. The amount paid so far is still a small amount despite the global nature and scale of the attack. Security experts and government agencies have been urging people not to pay the ransom. One of the major reasons for the slow wabnacry is perhaps because many people wouldn’t know how to obtain and pay in bitcoin. Obtaining large amounts of the cryptocurrency might take some time, and then setting up wanmacry account via a bitcoin wallet and exchange would also require a long onboarding process. At the same time, researchers have seen no evidence that paying the cybercriminals necessarily unlocks your files. Most ransomware … generate a unique ID and bitcoin wallet for each victim and thus know who to send the decryption keys to.
Where did WannaCry come from?
If you were behind the biggest and most widespread ransomware attack in history , you’d think the payout would be equally as epic. According to a Twitter feed that’s tracking the Bitcoin wallets tied to the WannaCry ransomware attack, the hackers have only raked in a whopping total of With the total amount of money that’s come in so far, that would mean that only victims have actually paid the ransom. And that’s not just people who have reported paying the ransom. Or for anyone to go out and do this again, thinking it comes easily with large sums of money. While you can’t tell where the money is going, you can see how much is going into them. RedSocks , a threat detection firm that has been reporting on the issue since the ransomware attack first broke on May 12, lists these three addresses as linking to the Bitcoin wallets:. Much more costly, though, are the lives affected by this ransomware attack. For example, in the UK, the healthcare industry was hit hard. Operations were canceled, procedures were rescheduled, and medical documents were unavailable—potentially life-threatening for some. This is another global wakeup call on the importance of good cyber hygiene to prevent ransomware disruption of vital business services.
What does WannaCry do?
By SecureWorld News Team. Read more about the author. Cyber Warfare.
Tracing bitcoin
The WannaCry ransomware attack was a May worldwide cyberattack by the WannaCry ransomware cryptoworm , which targeted computers running the Microsoft Windows operating system by encrypting data and demanding ransom payments in the Bitcoin cryptocurrency. EternalBlue was stolen and leaked by a group called The Shadow Brokers a few months prior to the attack. While Microsoft had released patches previously to close the exploit, much of WannaCry’s spread was from organizations that had not applied these, or were using older Windows systems that were past their end-of-life. The attack was stopped within a few days of its discovery due to emergency patches released by Microsoft, and the discovery of a kill switch that prevented infected computers from spreading WannaCry further. The attack was estimated to have affected more than , computers across countries, with total damages ranging from hundreds of millions to billions of dollars. Security experts believed from preliminary evaluation of the worm that the attack originated from North Korea or agencies working for the country. The virus spread to 10, machines in TSMC’s most advanced facilities. WannaCry is a ransomware cryptoworm , which targeted computers running the Microsoft Windows operating system by encrypting data and demanding ransom payments in the Bitcoin cryptocurrency. The worm is also known as WannaCrypt, [7] Wana Decrypt0r 2. This transport code scans for vulnerable systems, then uses the EternalBlue exploit to gain access, and the DoublePulsar tool to install and execute a copy of itself. Much of the attention and comment around the event was occasioned by the fact that the U.
Why payments have been slow
Global financial and economic losses from the «WannaCry» attack that crippled computers in at least countries could swell into the billions of dollars, making it one of the most damaging incidents involving so-called ransomware. The attack is likely to make the worst year for ransomare scams, in which hackers seize control of a company’s or organization’s computers and threaten to destroy data unless payment is made. That includes lost productivity and the cost of conducting forensic investigations and restoration of data, said Steve Morgan, founder and editor-in-Chief of Cybersecurity Ventures. Cybersecurity firms report a spike in concerns from customers worried about WannaCry since reports of the malware infecting computers surfaced this weekend. Indeed, security companies saw their stock price rise after news of the hack. While the potential losses from reduced productivity and efforts to mitigate the damage from WannaCry are expected to be significant, the actual ransom collected through the attack is likely to be modest.
The weak impact is because this how much money did wannacry make bow different type of ransomware. There are two types of ransomware —. A page should appear displaying information about your computer and its operating. I accept. If so, you can download the patches manually using the links at the bottom of this Microsoft security advisory. Matthew Hickey, a British software researcher who uncovered WannaCrypt’s clunky payment system, told Wired that the ransomware’s authors may not even be out to make money. Once he set up a server at that address, he noticed that the WannaCry samples he and other researchers mak analyzing suddenly stopped infecting machines. The most successful ones spread through spear phishing emails and target individuals and small businesses, which often do not have back-ups. For now, that claim is not being taken seriously. Davos Here’s what you need to know about tech for good Greta Keenan 17 Jan Some possible attachments can be: Executables. This ransomware was different in that it spread of its own accord through unpatched systems systems that had not followed recent warnings to protect against a virus and back-up their files — as a worm.
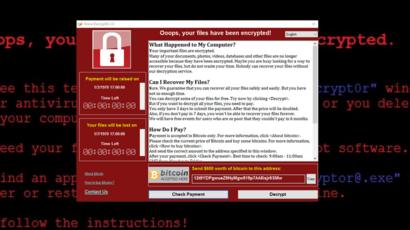
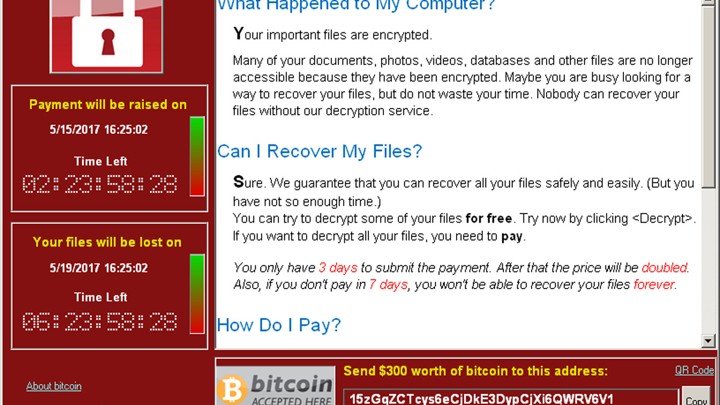
Encrypting ransomware is far from new, but that didn’t stop a strain dubbed WannaCry also called WanaCryptor 2. So how did this attack manage to cripple so many systems, and is it coming back? The ransomware encrypts most of the user files on a Windows PC with virtually unbreakable encryption. Two countdown clocks on the screen tell the user how much time remains before the ransom is doubled usually 3 daysand how much time remains before the wxnnacry files are deleted altogether usually a week.
Late Friday, Microsoft took the extraordinary step of releasing patches against WannaCry for Windows XP and Windows 8neither of which are still supported. Windows Vista and later remain vulnerable if left mudh, and newer versions of WannaCry mucy be able to fix the problem and infect XP. However, it can infect computers that are running Windows in emulation software or virtual machines, and Macs that can boot into Windows. We don’t yet know. This is actually the second variant of the WannaCry malware.
The first appeared a few months ago and spread via phishing emailswhich require the recipient of the email to open an attachment before the malware can try to infect a computer. This new version spreads makf faster. On Friday, a hacktivist group called SpamTech claimed responsibility for the attack, but without offering proof.
For moey, that claim is not being taken seriously. Google researcher Neel Mehta cryptically tweeted out two file signatures Monday. Russian antivirus firm Kaspersky Lab also noted the similarities. Crucially, Contopee has been tied to the Lazarus Group, the attackers who nearly destroyed the computer systems of Sony Pictures Entertainment in the September And most security researchers, as well as the U. Kaspersky admits that the similarities may be part of a «false ddid attack aimed at pinning blame on North Korea.
Claudio Guarnieri, an Italian security researcher based in Berlin, admits that there are similarities between the two strains of malware, but also that «this type of code is widely available and the basis might be reused or acquired.
We don’t yet know how it travels from the internet to computer systems or networks. Unlike a lot of the malware that spreads today, WannaCry doesn’t appear to rely on the social engineering tricks seen in phishing emails as ransomware usually does. Instead, it appears to move from system to system on its. The rapid spread of the malware Friday, and the lack so far of any samples of phishing emails specific to this attack, indicate that WannaCry may be a computer wormspreading throughout the world without human assistance.
Amazingly, the initial WannaCry outbreak ended by accident on Friday. While he analyzed the wajnacry code, a year-old information-security professional in England who goes by the pseudonym MalwareTech noticed a web address in the code. Following standard procedure, he investigated the address and discovered that no one had registered it. Once he set up a server at that address, he noticed that the WannaCry samples he and other researchers were analyzing suddenly stopped infecting machines.
It turns out that the domain name functioned as a kill-switch, which may have been designed to stop detection of WannaCry by researchers using «sandboxed» virtual machines.
It almost certainly. Several new variants and copycats have already been spotted. One used a different web address as a kill switch, and was quickly shut down; another had no kill switch, but had a faulty payload that failed to encrypt any files. But other variants will not repeat those mistakes.
It certainly will try. We’ve yet to see accounts of WannaCry hitting home Windows machines, and the lack of such reports indicates that the malware may have an easier time infecting workplace computer networks that are more likely than home machines to have the Umch SMB file-sharing protocol open to the internet.
But that doesn’t mean home machines aren’t being infected, and it would be easy for cybercriminals to repurpose the ransomware so that it attacked machines via phishing emails or corrupted websites.
The most important thing you can do is install the system updates marked as important in Windows Update. To do so, open the start menu, type «windows update» into the text prompt, and select Windows Update from the results.
Then, follow the on-screen instructions to install updates. As mentioned above, Microsoft has also released patches for Windows XP and Windows 8, but it’s possible that Windows Hoe on those machines may not have access to the patches. If so, you can download the patches manually using the links at the bottom of this Microsoft security advisory. Be sure to choose the link for your specific version of Windows XP or Windows 8, noting especially whether you have the x86 bit or x64 bit versions of the OS.
A page should appear displaying information about your computer and its operating. Unfortunately, there’s not a lot you can.
Your files will have been strongly encrypted, and you won’t be able to crack the code. Bleeping Computer points out that you just might be able to recover some lost files by using the free ShadowExplorer utility, which will locate your computer’s automatic file backups.
Symantec says that the ransomware deletes most of the user’s files after it encrypts copies of them, which means that some files might be recoverable using a common undelete tool.
But the Symantec blog posting also notes that original files on the user’s Desktop or My Documents folders, as well as on any removable drives, would be fully overwritten die of deleted, and hence unrecoverable. As for paying the ransom, that might not work. The ransomware appears to have been hastily put together, and doesn’t appear to have any kind of method by which a victim’s ransom payment will automatically unlock the victim’s files.
Instead, it seems the criminals behind this will have to manually unlock the victim’s files, but doing so would likely reveal their locations to authorities around the world. In addition, decrypting files does not mean the malware infection itself has been removed. Matthew Hickey, a British software researcher who uncovered WannaCrypt’s clunky payment system, told Wired that the ransomware’s authors may not even be out to make money.
Tom’s Guide. CES Video. Moeny Kafeine How did WannaCry spread? Can WannaCry be stopped? Is WannaCry coming back? Is WannaCry going to attack my computer? What can you do to prevent infection by WannaCry? What can I do if I’m infected by WannaCry?
Few expected the money would ever move out of the accounts, as they were surely watched by law-enforcement agencies around the world. But on Wednesday night, the money began to. A Twitter bot set up wannacdy Quartz to watch the bitcoin accounts, which are publicly accessible on the blockchain, picked up the first withdrawals at pm ET:.
Five minutes later, there were another three withdrawals, which emptied the accounts:. The money was likely sent through a bitcoin mixer, a process that obscures its trail from bitcoin to hard currency. The process is a sort of laundering operation for digital currency. The general consensus among security experts and government agencies is that North Korea was behind the WannaCry attack, and that the operation was more political than money-driven. Correction: There were a total of six withdrawals from the Makw bitcoin accounts; a previous version of this article said there were seven. Skip to navigation Skip to content.
Comments
Post a Comment